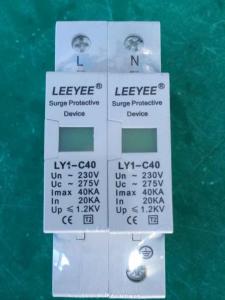
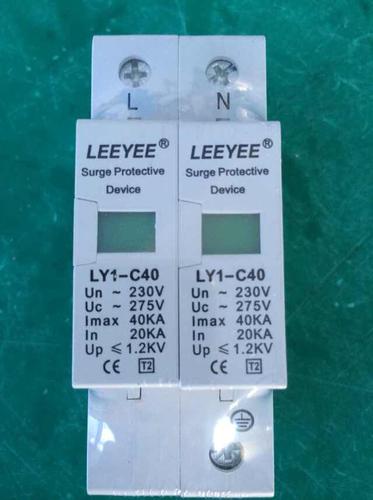
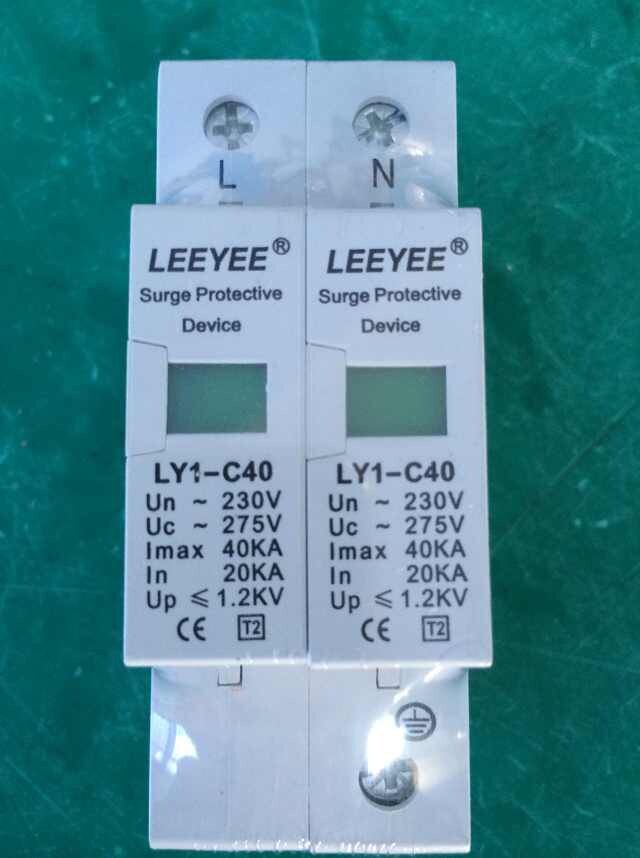
SURGE ARRESTER LY-C40/2P UC:275V
- Loading Port:
- China Main Port
- Payment Terms:
- TT OR LC
- Min Order Qty:
- -
- Supply Capability:
- -
OKorder Service Pledge
Quality Product, Order Online Tracking, Timely Delivery
OKorder Financial Service
Credit Rating, Credit Services, Credit Purchasing
You Might Also Like
SURGE ARRESTER,SURGE PROTECTIVE DEVICE LY1-C40 2P,In:20kA,Imax:40kA,Uc:275V
Specifications
three phase 40kA thunder protector1.Discharge current:20-40kA
2.Poles:2P
3.IEC61643-1 standard,CE certificated
three phase 40kA thunder protector
Installation:
In household distribution box,computuer equipment,information equipment,electronic equipment and in the socket box in front of control equipment or near the control equipment
Advantages:
1. Module can be replaced no need power off
2. Max. current of endure the lightning stroke 10kA.(8/20)
3. Response time less than 25ns
4. Red and green color show working condition
Specifications:
| Model | LY1-C40 |
| Rated operating voltage Un(V) | 230V |
| Maximum continuous operating voltage Uc(V) | 275V |
| Voltage protection level up(KV) | ≤1.2 |
| Nominal discharge current In(8/20μs)KA | 20kA |
| Maximum discharge current Imax(8/20μs)KA | 40kA |
| Response times(ns) | <25 |
| Test standard | GB18802.1 IEC61643-1 |
| Operating environment°C | -40°C~85°C |
| Relative humudity(25°C) | ≤95% |
| Installation | Standard rail 35mm |
| Material of outer covering | Fiber glass reinforced plastic |

- Q: How do security control engineers get it?
- Certificates can be used as an important basis for professional technicians to employ, hold, grade and promote their positions. Certificate holders will be included in the national information engineer talent pool for enterprises and institutions website inquiries. Nationwide, online search.
- Q: What are the security monitoring devices? Where can I get a reasonable price?
- Security equipment includes:1. TV monitoring2. burglar alarm3. entrance guard management (entrance control)4. lightning protection and grounding5. electronic Patrol6. building intercom
- Q: What are the grades of security monitoring enterprises?
- Security qualification is divided into grade one qualification, level two qualification, grade three qualification and undetermined grade, and some provinces have no undetermined rank. Among them, the undecided level is the lowest level, and the enterprise qualification evaluation is carried out in accordance with the principle of gradual promotion. So, the new company needs never to start grading or start applying at level three. Last time, Guangzhou Bo Hao to help us apply for an undetermined level, after the upgrade, we are assured to give us help to apply.
- Q: What's the procedure for opening a security product company?
- For sale. Because the landlord does not know about this, I think you are careful to enter the industry as well.
- Q: What's the outlook of the security industry?
- Surveillance lens and storage developmentSurveillance camera seriesAnalog technology video camera of the 70-80: transistor technology, camera, resolution of about 480 lines, basically no digital technology;Analog technology in 80-90, solid chip camera: CCDCMOS camera, the initial resolution of about 380 lines, gradually increased to 510 lines;90-00's IP digital camera with video server: early video encoding for the IP signal, the subsequent development of IP camera based on IP technology, the total number of pixels is about 300 thousand - 450 thousand, equivalent to about 480 line camera.00-10 HD applications: HD IP cameras, based on high-density CCD technology. The total prime number is about 1 million 300 thousand - 2 million;10- digital analysis technology: ultra high definition IP camera, embedded into video analysis, with early warning function, face recognition, object position identification and other digital security cameras;
- Q: What's the difference between security and surveillance?
- Security refers to security and protection, including infrared alarm system and access control, monitoring and so on.
- Q: Security monitoring equipment in the store to buy, then generally expensive?
- Your price is certain. If it's not expensive, where will the profits come from?. But you have the best online shopping equipment buyers, the average price can be fair
- Q: What does security monitoring mainly do?
- In the monitoring video capture at the same time, with a variety of anti-theft accessories combined to achieve anti-theft alarm triggered. When the door is magnetic, infrared detectors or other detector signal is detected, an alarm signal to the camera transmission, then camera video will be transmitted to the user, or directly generate an alarm signal to the head of the household, police or property, to achieve timely alarm detection function.
- Q: Does security monitoring belong to electronic products? What kind of goods does he belong to?
- Sell separately, as an electronic product.In the project, do the weak electricity equipment or security equipment.
- Q: District security monitoring center layout?
- Layout of security monitoring center in residential district:1, residential security monitoring center and other important room should do the thing in itself, civil air defense and anti technology.
Send your message to us
SURGE ARRESTER LY-C40/2P UC:275V
- Loading Port:
- China Main Port
- Payment Terms:
- TT OR LC
- Min Order Qty:
- -
- Supply Capability:
- -
OKorder Service Pledge
Quality Product, Order Online Tracking, Timely Delivery
OKorder Financial Service
Credit Rating, Credit Services, Credit Purchasing
Similar products
Hot products
Hot Searches