Laptop Lock Notebook Lock with Multi-Faceted Rotation
- Loading Port:
- China Main Port
- Payment Terms:
- TT or LC
- Min Order Qty:
- 500 Pieces 10000 pc
- Supply Capability:
- 80000 Pieces per Month 100000 pc/month
OKorder Service Pledge
OKorder Financial Service
You Might Also Like
Specifications
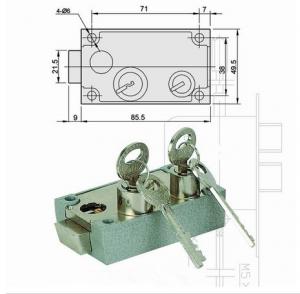
Laptop LockNotebook Lock with Multi-faceted rotation and 4compose combination ,quality: ROHS,CE,
1.body lock size: 46*18*11mm
2.steel wire size: diameter Φ3mm(4,5,6mm)*1200(1800,2000,2500)mm
3.the laptop lock with master key.
|
|
|
| ||
| Item NO | Combination Laptop lock | |||
Description |
AL-C4000(BODY LOCK SIZE:diameter Φ14mm×L23mm) | ||||
Size (cm) | Φ5MM*1800MM (1000MM,1200MM,1500MM,2000MM) | ||||
FOB USD | USD3.2/PCS(FOB PRICE ) | ||||
Packaging | 60pcs/cnt (40*30*20cm) NG:10.8KG WG:11.8KG | ||||
pcs/g | 200g/pcs | ||||
Lead Time | 7 days | ||||
Payment Term | T/T,LC | ||||
Minimum order quantity | 1000pcs | ||||
Certificate | ISO9001-2000,CE,ROHS | ||||
Material | Brass +steel + zinc alloy material | ||||
- Q:Germany KLC door lock quality is good
- Ten years old brand, and sell things out of word of mouth are also good. Sold a lot of brand a lot of products, but also eliminated a lot of brands. Klc is what I've been selling. Often bought a few years ago for home decoration for the house to buy again.
- Q:Inside the hotel door lock called what lock
- Chain buckle installed in the back of the door from the door near the place, one end of the chain chain fixed on the door frame, the other end is active, can be inserted into the back of the chain buckle lock. When the anti-theft chain, the door can only open to the maximum of 5 to 8 cm, people can not pass, the hand can not be reached from the door enough to the back of the chain buckle, which ensures that the owner in the door to confirm the visit When the identity, will not be the other side of the sudden attack.
- Q:What is the tube well lock
- Tube lock is also called simple door locks, universal door locks, pipe doors, electrical doors, line doors and other special locks.
- Q:What is the meaning of the safety of the gas stove?
- Open the child lock, the children on the stove on the ignition or switch will not open the gas stove to avoid children injured. When igniting, first touch the child lock knob and then ignite the gas stove.
- Q:Yue Ma lock good? Yue Ma lock is not expensive
- Especially their 750 leaf lock series, whether it is old-fashioned door or gourd do not have to do a good job. As for the price of course is not cheap, the price is in the country, the middle reaches.
- Q:What documents do you need to produce a lock?
- Home lock, mortise lock, car lock, chain lock, garage lock, safe lock, electronic lock and so on, according to your customer needs, technical ability, production capacity to decide it, free market free choice.
- Q:Separation lock and split lock
- Split locks can sometimes be expanded into a collection of locking blocks, and they belong to separate objects, which is the separation of locks.
- Q:Rotary safe password lock has a password
- Rotate in a counterclockwise direction for one week and then continue to rotate (20) to the mark line above;
- Q:What are the characteristics of anti-theft lock
- If the key lever is dazzle without teeth, this lock is a magnetic lock, in fact the key head of the whole set of a casing, remove the casing can see the above mosaic with three to five small dots. Magnetic lock is very solid, cross lock is very convenient to open. The market can buy special tools for opening magnetic locks and cross locks. With this tool, thieves can open most of the magnetic locks and cross locks in a minute or two. Computer lock complex lock more secure, computer lock is just a professional name, not really use the computer to unlock. Computer lock keys have three to five ranging from the circular groove, the groove is the combination of factory computers out, so called the computer lock. Different manufacturers, the computer used by the program are mostly different, hit out of the groove where the location, size, depth is not the same natural, so its mutual open rate than the cross lock, a word lock much lower. Even unlock the master, open a computer lock time also in ten minutes or so. There is also a more secure anti-theft door lock, that is, composite lock. The so-called composite lock is the combination of two or more different principles of the lock cylinder in the same lock.
- Q:How to use it correctly
- Appearance Maintenance: 1. During the renovation of the house, please use the plastic bag (do not bring the plastic tape with the plastic surface and the lock surface contact) to seal the lock handle, panel and other exposed parts, so as not to lock the surface treatment layer Decorative with acidic or alkaline materials and gas erosion caused by spots, blistering or even delamination phenomenon, seriously affect the appearance of the quality of the lock. Some zinc alloy and copper locks, installed on the door for a long time will find a "spot", this phenomenon does not belong to rust, but belongs to oxidation, if this happens, as long as the surface wax spray You can remove the spots. 2, the normal use, if dirt, dry cloth can be used to clear, do not use detergent and other chemicals scrub. Otherwise, will destroy the protective film of the exposed parts, causing fading. Do not use a damp cloth to wipe the lock body and handle, because some metal material locks will be rusty; alloy material lock will wear off the coating, loss of beautiful results.
1. Manufacturer Overview |
|
|---|---|
| Location | Zhejiang,China (Mainland) |
| Year Established | 1998 |
| Annual Output Value | US$2.5 Million - US$5 Million |
| Main Markets | North America 25% South America 25% Eastern Europe 12% Southeast Asia 10% Africa 5% Oceania 5% Western Europe 16% South Asia 2% |
| Company Certifications | ISO9001 Certificate |
2. Manufacturer Certificates |
|
|---|---|
| a) Certification Name | |
| Range | |
| Reference | |
| Validity Period | |
3. Manufacturer Capability |
|
|---|---|
| a)Trade Capacity | |
| Nearest Port | Ningbo, Shanghai |
| Export Percentage | 61% - 70% |
| No.of Employees in Trade Department | |
| Language Spoken: | English, Chinese, Japanese, German, French |
| b)Factory Information | |
| Factory Size: | 3,000-5,000 square meters |
| No. of Production Lines | 8 |
| Contract Manufacturing | OEM Service Offered Design Service Offered Buyer Label Offered |
| Product Price Range | Average |
Send your message to us
Laptop Lock Notebook Lock with Multi-Faceted Rotation
- Loading Port:
- China Main Port
- Payment Terms:
- TT or LC
- Min Order Qty:
- 500 Pieces 10000 pc
- Supply Capability:
- 80000 Pieces per Month 100000 pc/month
OKorder Service Pledge
OKorder Financial Service
Similar products
New products
Hot products