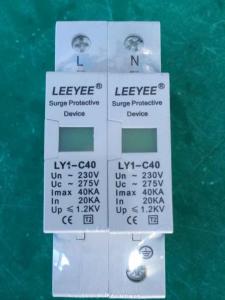
SURGE ARRESTER LY-C40/3P DC 1000V
OKorder Service Pledge
Quality Product, Order Online Tracking, Timely Delivery
OKorder Financial Service
Credit Rating, Credit Services, Credit Purchasing
You Might Also Like
SURGE ARRESTER,SURGE PROTECTIVE DEVICE LY1-C40,DC1000V.In:20kA.Imax:40kA
Specifications
1000V DC surge arrester1.For PV system lightning protection
2.In:20kA,Imax:40kA
3.PE connection
1000V DC surge arrester
Specification:
Features::
1. Plug in/out style surge protective device.
2. The color of visible window shows operating status.
3. Double protection of over-heat and over-current.
4. Have remote signal accessory, realize remote control.
Product photos:


- Q:General security monitoring, construction costs accounted for the total amount of equipment?
- Reasonable profit is about 15%. The main purpose of the business is to talk about the business, not to scare customers away. Of course, the customer is the boss your brother-in-law said, your brother-in-law when construction costs at 50%, he had to pinch your nose swallow
- Q:What's the difference between security and surveillance?
- The scope of security is relatively large, out of surveillance, there are perimeter alarm, intrusion detection systems
- Q:After graduation, I was very confused in the end is what kind of security monitoring industry, in a lot of recruitment websites all can not find a suitable location, who can give me a specific introduction, in the end is what industry specific prospect?
- Now relatively good is the intelligent building bar, comprehensive monitoring, alarm, fire, building intercom, integrated wiring and a series of integrated projects. The foreground is very good. At present, our country is in the initial stage, and now the new design of the building is a lot of intelligent, you can learn from this.
- Q:Who knows security monitoring common faults and solutions?
- Can first separate the monitoring system, 1 first check the front-end equipment, with engineering treasure to connect the camera, there is no ripple, not in the use of monitoring power supply project, treasure access surveillance video. If there is no front end, no problem. After processing the back end, insert the rear video line directly into the engineering treasure video, if not, that is the problem on the hard disk video recorder, if you have one. That's the transmission part. The transmission section can see whether the video lines have power jamming devices, powerful electric power, signal communication towers and so on. Some words can be wire principle interference source or install galvanized tube, reduce electromagnetic interference, or use video anti-interference device and so on.
- Q:What are the security monitoring devices? Where can I get a reasonable price?
- 1. intrusion detector:Active infrared intrusion detector and passive infrared intrusion detector, microwave intrusion detector, microwave and passive infrared intrusion detector, ultrasonic intrusion detector, vibration intrusion detectors, magnetic switch intrusion detectors, ultrasonic and passive infrared intrusion detector.2. burglar alarm controller:Including wired, wireless anti-theft alarm control, transmission, display, storage and other equipment.
- Q:I would like to open a security monitoring store, you need to go through what procedures?
- For individual industrial and commercial registration, you can apply for industrial and commercial registration documents, fees are probably more than 100 yuan
- Q:How many lines are there in the security monitoring system?
- You can't control the camera lens, only video cable and power line,If the camera does not rotate, just two linesVideo cable and power cordAdd signal control line if rotating
- Q:What data does security monitoring and bidding require?
- (4) the copy of the legal person's power of attorney and identity card of the bidder;(5) the principal agent and after-sale service certificate of the main equipment;(6) information about the tenderer's profile;(7) part of the list of users in recent years.Note: all photocopies of the above documents should be stamped with the official seal of the unit, and the tenderee shall keep it.
- Q:How does the security monitoring system go through the line?
- Bright dark line details: bridge design is reasonable, to ensure the appropriate cable bending radius. When the upper and lower sides are around the other line grooves, the slope of the turn should be gentle, and the key point is that the cable at both ends will sag. After the force is applied, the cover plate can also be laid on the premise that the cable is not damaged.On line process is mainly control the tension, the tape reel cable, at least two suggestions to arrange for a worker to scroll in Guyed pole homemade, line end workers first pulled out a part of the cable from the scroll box for the pipeline in the pre, the other end of pre extraction. Pull out of the line can not be too much, to avoid entanglement with a plurality of lines on the ground around.
- Q:What are the sales methods of security engineering?
- The overall marketing methods of security products include supplier marketing, distributor marketing, final customer marketing, and staff marketing.
1. Manufacturer Overview |
|
|---|---|
| Location | |
| Year Established | |
| Annual Output Value | |
| Main Markets | |
| Company Certifications | |
2. Manufacturer Certificates |
|
|---|---|
| a) Certification Name | |
| Range | |
| Reference | |
| Validity Period | |
3. Manufacturer Capability |
|
|---|---|
| a)Trade Capacity | |
| Nearest Port | |
| Export Percentage | |
| No.of Employees in Trade Department | |
| Language Spoken: | |
| b)Factory Information | |
| Factory Size: | |
| No. of Production Lines | |
| Contract Manufacturing | |
| Product Price Range | |
Send your message to us
SURGE ARRESTER LY-C40/3P DC 1000V
OKorder Service Pledge
Quality Product, Order Online Tracking, Timely Delivery
OKorder Financial Service
Credit Rating, Credit Services, Credit Purchasing
Similar products
New products
Hot products